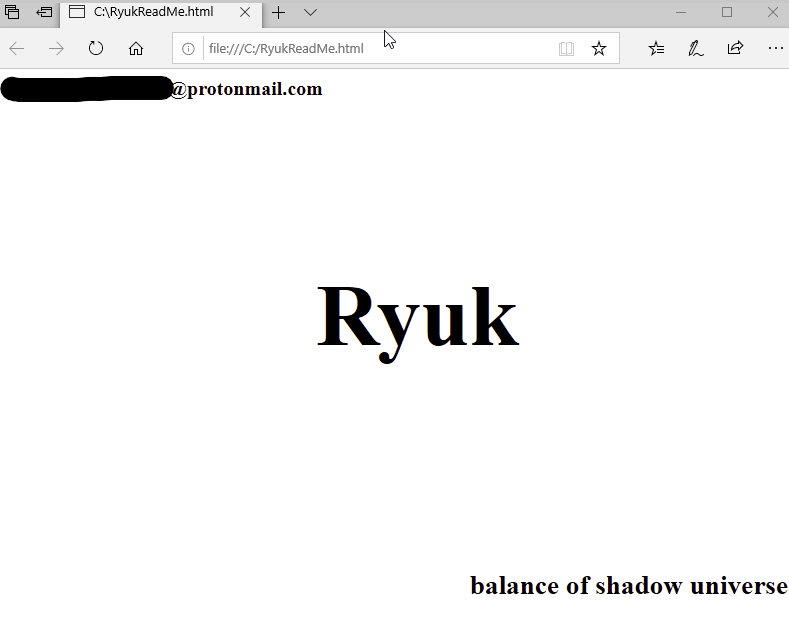
A few days ago, I ran a Trickbot sample in the lab and was quite surprised what occurred. The attackers ran Cobalt Strike across multiple machines within 30 minutes and confirmed hands on activity within 60 minutes. They did additional recon and testing before deploying Ryuk. The attackers were able to go from Trickbot on…
Zeppelin Ransomware
An attacker logged into the honeypot and dropped/ran Zeppelin within 5 minutes of logging in. Zeppelin is from the VegaLocker/Buran family. More info can be found at cylance.com and bleepingcomputer.com. According to bleepingcomputer, affiliates earn 75% of the ransom payment while the operators would earn 25%. Here’s some info from the attack. Attacker logged in…
Iranofficall User Creator Script
This script was dropped and run in the honeypot recently. Here are a couple takeaways and a screenshot of the script. @iranofficall / User Creator Adds 4 users Sets passwords to $95But6nL03 Sets passwords to never expire Enables RDP Hides accounts from sign-in screen Possible Detections Command arguments contains /maxpwage:unlimited Process net.exe + command arguments…
Harma and Odveta Ransomware
The attacker logged in from 64.44.81[.]20 and dropped two files. One named ours.zip and the other named 2284JS_payload.zip. They then attempted to extract these files numerous times but Defender blocked them. The attackers were not successful in their mission of deploying ransomware on the system. Here’s some brief information on the two variants and IOCs….
Interesting Recon Script
An attacker dropped and ran a recon script named new1.bat. The script deleted itself after it ran but due to logging I was able to see most of the commands it ran. A list of commands can be found here. I was able to locate at least a portion of the script which was posted…
Trickbot and AdFind Recon
An attacker logged into the honeypot, dropped AdFind, a couple batch files and Trickbot. The attacker created a user, ran a recon script utilizing AdFind and then installed Trickbot. This is what the folder structure looked like. Timeline Time in UTC 22:13 – login from 216.170.123[.]19 22:15 – opens powershell and runs the following command…
The Dever Ransomware Experience
I was scrolling through social media the other night and came across a friend who posted a screenshot of one of his home lab devices getting ransomwared. I reached out and asked if he wanted help taking a look into what happened and he excitedly said yes! The next 7-8 hours were a blur. I…
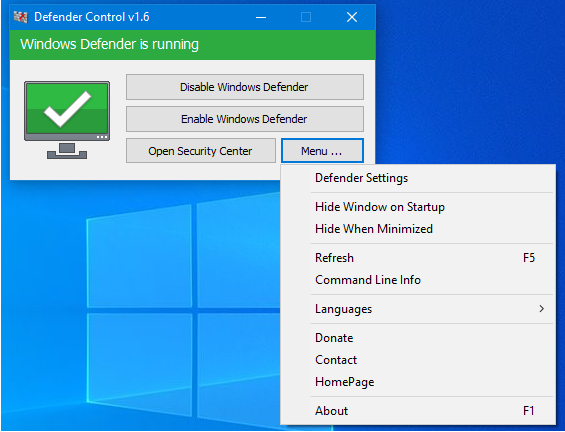
VBS Downloader and Defender Control
An attacker logged into the honeypot and ran a batch file that created a vbs script that attempted to download a possible coin miner. The download was blocked by the content filtering system but the attacker seemed to think Defender blocked it. The attacker then downloaded an application named Defender Control to turn off Defender….
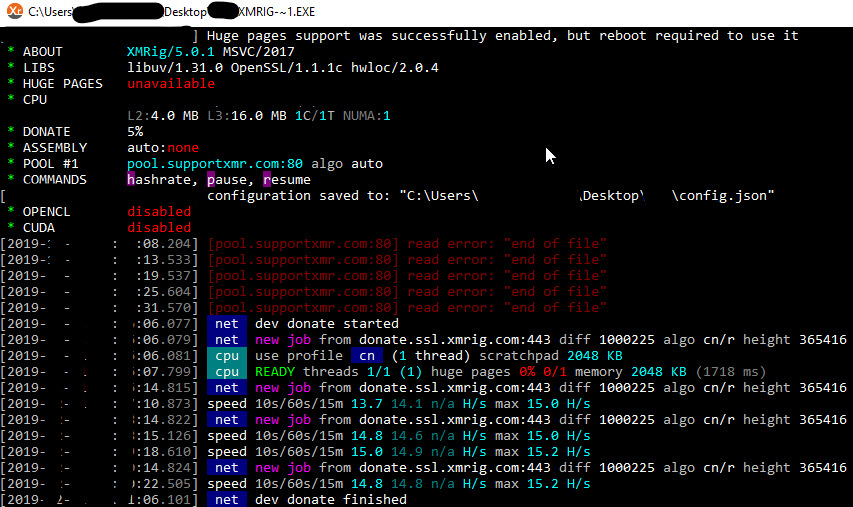
XMRig and OPSEC Fail
An attacker logged into the honeypot, dropped XMRig and mimikatz, and then ran XMRig. XMRig installed Netshta to maintain persistence and then started mining Monero. When the attacker dropped mimikatz, they accidentally dropped a list of usernames, passwords and IPs. See below for info on XMRig, intrusion summary, OPSEC fail, and IOCs. XMRig XMRig is…
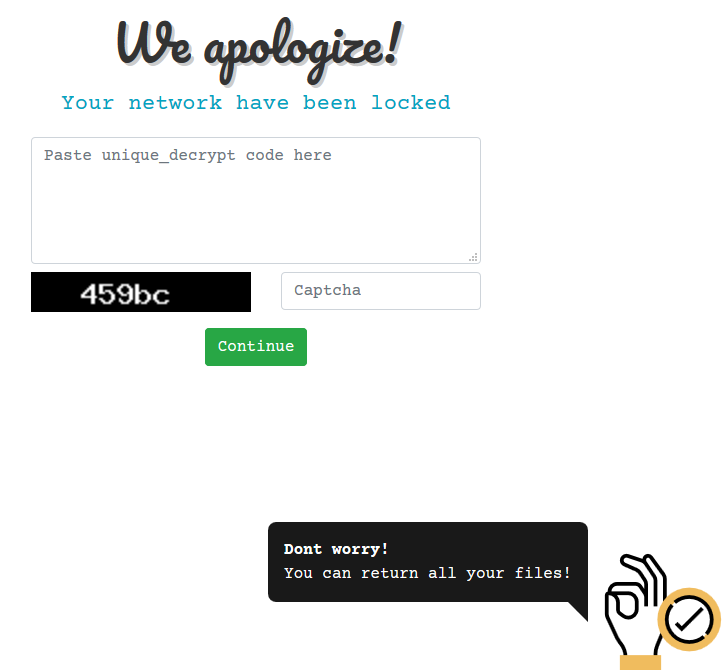
Ako Ransomware
An attacker logged into the RDP Honeypot and quickly ran Ako Ransomware. The attacker had opened the Defender GUI to disable it–but a bot from the previous day had already disabled it. The attacker then dropped Locker.exe, ran it, and then logged off before the execution had completed. Locker.exe is also known as Ako and…